Vunwabilwity 🥺
I'm always trying to understand how applications work under the hood. When I noticed the MSU-IIT MICA website was loading slower than usual, I started tinkering to see if I could identify bottlenecks. This casual investigation would lead me to uncover a critical vulnerability exposing the private data of thousands of students.
It started when I was examining the website's network traffic and API calls. I noticed it was fetching student information and prospectus details from endpoints like these:
- GEThttps://micaapi.msuiit.edu.ph/api/prospectus?studid=[idnumber]
- GEThttps://micaapi.msuiit.edu.ph/api/get_info?studid=[idnumber]
Out of curiosity, I tried modifying the student ID number parameter to see if I could access records for students I didn't have any affiliation with. To my surprise, I was able to retrieve full details simply by changing the ID. I soon realized I had stumbled upon a major Insecure Direct Object Reference (IDOR) vulnerability.
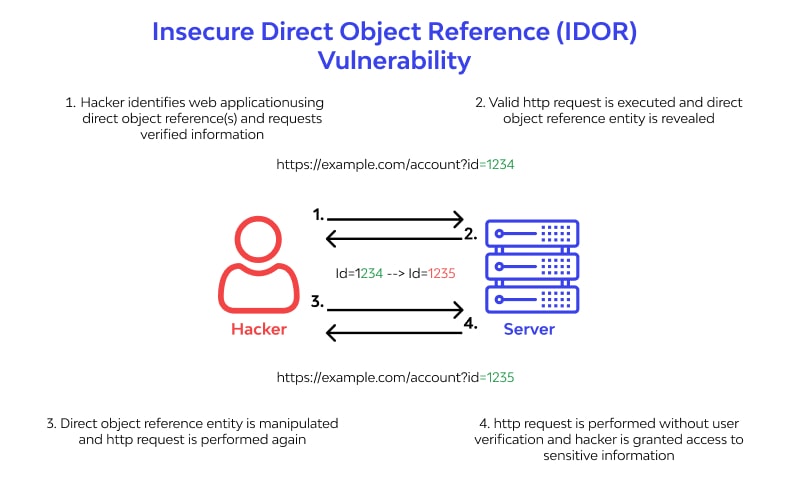
The MICA API was failing to properly authorize requests based on the authenticated user's permissions and affiliation to the student ID being requested. This meant an authenticated user could freely access the private records of any student by simply modifying the ID number value, a significant breach of privacy and security.
Building a Data Retrieval Tool
To gauge the full scope of this issue, I created a Python script that could rapidly retrieve student data across a wide range of ID numbers. The tool uses multithreading to concurrently fetch records for all MSU-IIT ID numbers.
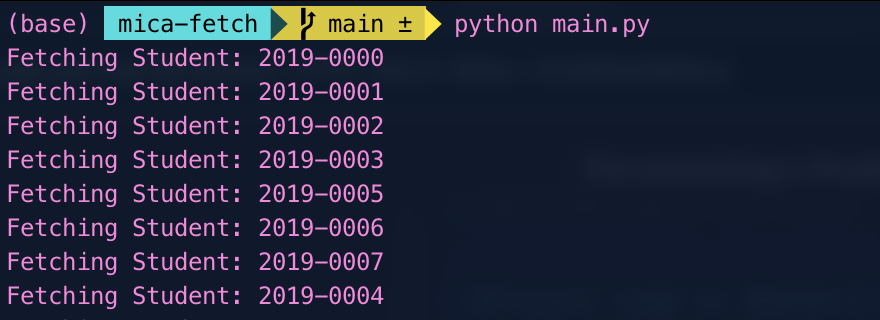
As it retrieves data from the vulnerable API endpoints, mica-fetch saves the sensitive student information and prospectus details to local JSON files organized by ID number. This provides clear evidence of how an authenticated user could exploit the IDOR vulnerability to mine and export comprehensive records.
Of course, my intention was never to actually obtain or disclose this private student data improperly. The mica-fetch tool was built solely to systematically demonstrate the reality of the vulnerability to the MSU-IIT team for remediation purposes.
Responsibly Disclosing the Findings
After documenting the issue thoroughly with mica-fetch, I immediately initiated responsible vulnerability disclosure procedures with the MSU-IIT staff. I provided a complete proof-of-concept demonstrating how I could access any student's data through the flawed API authentication model.
To their credit, the team took my findings seriously and has been working to implement rigorous access controls and permission checks for the MICA API.
This experience was a vivid example of why developers need to uphold robust privacy and security practices, especially when building applications that handle sensitive user data. I'm grateful I was able to catch this vulnerability before it could be maliciously exploited. But we must remain vigilant to find and responsibly disclose similar vulnerabilities that could compromise people's personal information.